Most of the time you find yourself wishing for a single window where you
could view and manage all of these diverse sources of information. And
that is exactly where Microsoft Message Analyzer comes to your aid.
Microsoft has ensured that the Message Analyzer stays relevant and
powerful with time. That’s why beginning with Windows 8.1/2012, the
tool’s capture driver is integrated with the Windows operating system.
What this signifies is effective WinRM configuration – the kind you are
able to capture using a remote machine. That’s not all! You are now able
to capture from more than one machine at the same time.
When you’re beginning a new live trace, you have the option of editing the target systems and entering either the IP or the name of the computer you actually want to capture from.
There’s another method you can use to capture. This involves capturing at the Windows Firewall level prior to the local IPsec encryption, or even at the actual application level before it gets encrypted by HTTPS.
If you thought Microsoft Message Analyzer’s capabilities ended with
catching HTTP and IPsec traffic, you were wrong – that was only the
beginning. This tool allows you to perform captures or traces that you
can use to troubleshoot SMB directly, along with Bluetooth and USB.
At the time of setting up the trace, make sure you pick only the required trace scenario out of multiple options. That’s all you need to do! Moreover, this tool is capable of intelligent operations, checking the messages for anomalies, errors, or warnings with the utmost care.
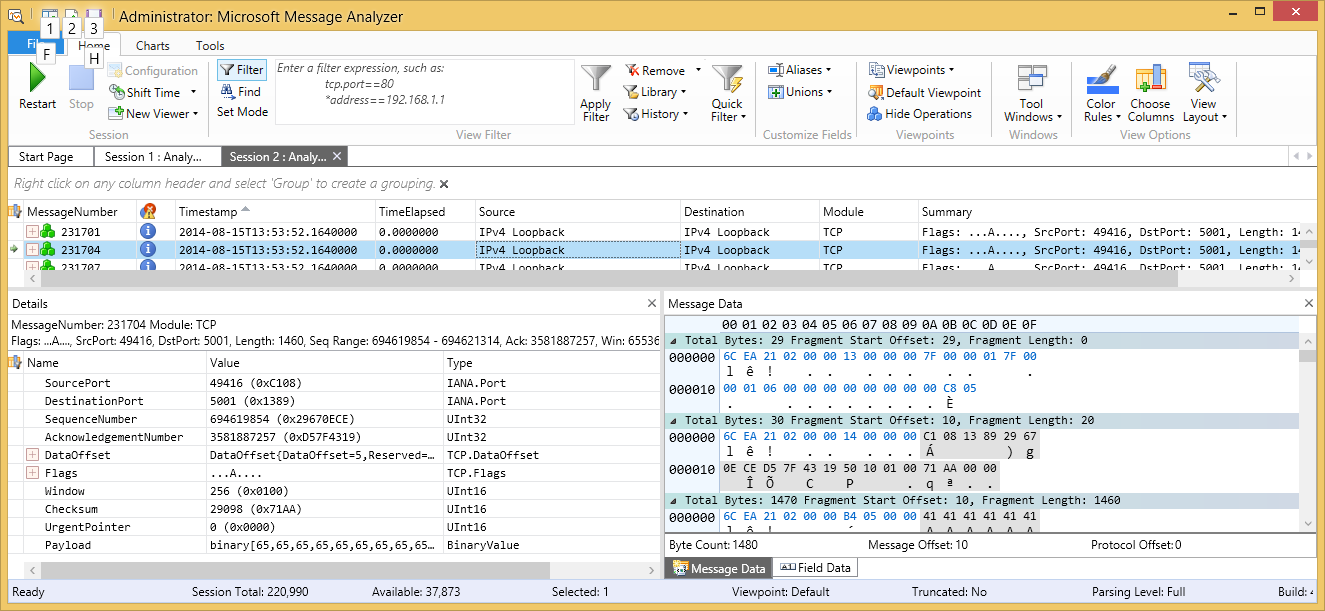
You are able to choose between the views that provide information as per your demand. In fact, there are a couple of views that enable you to look at the timing of the packets, the associated responses, along with the kernel module as well as the process name.
An amazing interface
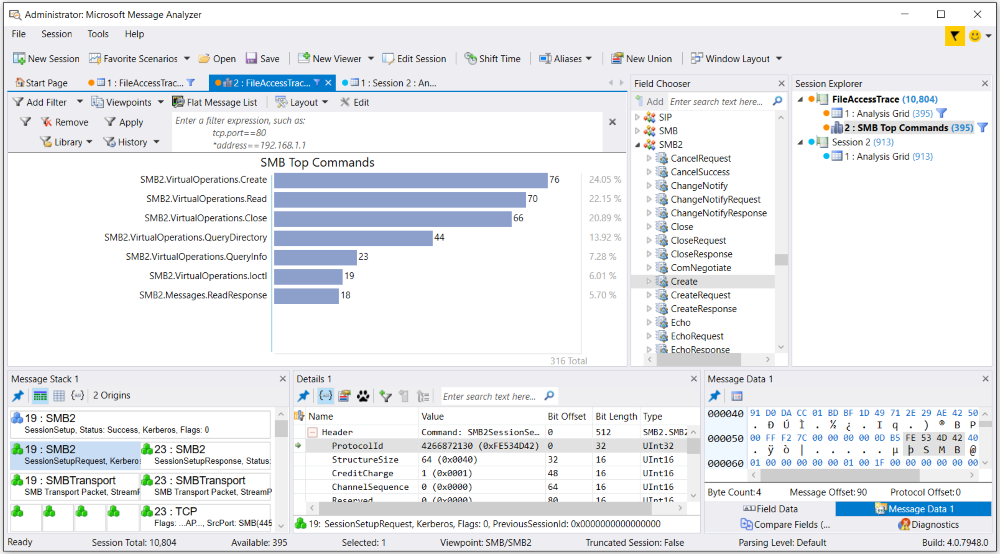
As the name implies, the “message” forms the basis of data. This
“message” takes on different formats, ranging from a captured frame or
packet to an event found on Event Viewer. You are able to merge or
“stack” these messages into conversations and sessions.
Remote capture capabilities
When you’re beginning a new live trace, you have the option of editing the target systems and entering either the IP or the name of the computer you actually want to capture from.
There’s another method you can use to capture. This involves capturing at the Windows Firewall level prior to the local IPsec encryption, or even at the actual application level before it gets encrypted by HTTPS.
More intelligence to better handle different scenarios
At the time of setting up the trace, make sure you pick only the required trace scenario out of multiple options. That’s all you need to do! Moreover, this tool is capable of intelligent operations, checking the messages for anomalies, errors, or warnings with the utmost care.
You are able to choose between the views that provide information as per your demand. In fact, there are a couple of views that enable you to look at the timing of the packets, the associated responses, along with the kernel module as well as the process name.
Aucun commentaire:
Enregistrer un commentaire